There are below deployment patterns
· Performance Patterns
o Web Farms
o Application Farms
o Load Balancing Cluster
Consider the use of Web farms or Load Balancing Clusters, when designing a Scale Out strategy.
· Reliability Patterns
o Fail-Over Cluster
· Security Patterns
o Impersonation/Delegation
o Trusted Subsystem
o Multiple Trusted Service Identities
Performance Patterns:
WebFarm & Affinity:
A Web farm is a collection of servers where each server replicate/run the same application.
Requests from clients are distributed to each server in the farm, so that each has approximately the same loading.
Depending on the routing technology used, it may detect failed servers and remove them from the routing list to minimize the impact of a failure.
In simple scenarios, the routing may be on a "round robin" basis where a DNS server hands out the addresses of individual servers in rotation.
Figure 3 illustrates a simple Web farm where each server hosts all of the layers of the application except for the data store.
In Non-distributed Achitecture - Scaling out Web servers in a Web farm
Affinity and User Sessions
Web applications often rely on the maintenance of Session State between requests from the same user.
A Web farm can be configured to route all requests from the same user to the same server – a process known as Affinity – in order to maintain state where this is stored in memory on the Web server.
However, for maximum performance and reliability, you should use a separate session state store (SqlServer/StateServer) with a Web farm, to remove the requirement for affinity.
Application Farms
In Distributed Deployment , where the Business & Data layer runs on different physical tiers from the Presentation layer, Application Farm is used to Scale Out the Business & Data layer.
Similar to Web-Farm, Application-Farm is a also collection of servers where each server replicate/run the same application.
Requests from clients(presentation tier) are distributed to each server in the farm, so that each has approximately the same loading.
Load Balancing Cluster
Application/Service can be installed onto multiple servers that are configured to share the workload, as shown below.
This type of configuration is a Load-Balanced Cluster.
Load balancing Scales The Performance of server-based programs, such as a Web server, by distributing client requests across multiple servers.
Load balancing technologies, commonly referred to as Load Balancers, receive incoming requests and redirect them to a specific host if necessary.
The Load-Balanced Hosts concurrently respond to different client requests, even multiple requests from the same client.
For example, a Web browser may obtain the multiple images within a single Web page from different hosts in the cluster. This distributes the load, speeds up processing, and shortens the response time to clients.
Reliability Patterns
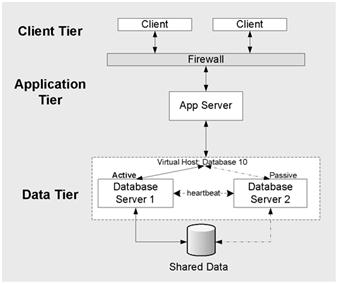
Reliability deployment patterns represent proven design solutions to common reliability problems. The most common approach to improving the reliability of your deployment is to use a fail-over cluster to ensure the availability of your application even if a server fails.
Fail-Over Cluster
A Failover Cluster is a set of servers that are configured so that if one server becomes unavailable, another server automatically takes over for the failed server and continues processing.
Application/Service can be installed onto multiple servers that are configured to take over for one another when a failure occurs.
The process of one server taking over for a failed server is commonly known as Failover. Each server in the cluster has at least one other server in the cluster identified as its standby server.
Security Patterns
Security patterns represent proven design solutions to common security problems.
Impersonation and Delegation approach is a good solution when you must flow the context of the original caller to downstream layers or components in your application.
Trusted Subsystem approach is a good solution when you want to handle authentication and authorization in upstream components and access a downstream resource with a single trusted identity.
Trusted Subsystem approach is a good solution when you want to handle authentication and authorization in upstream components and access a downstream resource with a single trusted identity.
Impersonation/Delegation
In the impersonation/delegation authorization model, resources (such as tables and procedures in SQL Server) and the types of operation (such as read, write, and delete) permitted on such each resource are secured using Windows Access Control Lists (ACLs) or the equivalent security features of the targeted resource.
Users access the resources using their original identity through impersonation, as below.
The impersonation/delegation authorization model
Trusted Subsystem
In the trusted subsystem (or trusted server) model, users are partitioned into application defined, logical roles.
Members of a particular role share the same privileges within the application.
Access to operations is authorized based on the role membership of the caller.
With this role-based (or operations-based) approach to security, access to operations (not back-end resources) is authorized based on the role membership of the caller.
Roles, analyzed and defined at application design time, are used as logical containers that group together users who share the same security privileges or capabilities within the application.
The middle tier service uses a fixed identity to access downstream services and resources, as illustrated in below Figure.
Multiple Trusted Service Identities
In some situations, you may require more than one trusted identity. For example, you may have two groups of users, one who should be authorized to perform read/write operations and the other read-only operations. The use of multiple trusted service identities provides the ability to exert more granular control over resource access and auditing, without having a large impact on scalability.
Reference: MS Patterns & Practices - Web Application Architecture Guide
Hope this helps.
Regards,
Arun Manglick





No comments:
Post a Comment